Starting with Windows 8, Microsoft introduced a new way to sign-in by using the online credentials to the user’s Microsoft Account. To help secure the user's account, Microsoft developed an additional authentication system, Windows Hello. In Windows 8, Windows 10 and Windows 11 users are encouraged to set up a PIN and use it instead of a password.
Elcomsoft System Recovery offers a built-in tool to brute-force Windows Hello PIN codes consisting of 4-6 digits. To break longer PIN codes as well as alphanumerical PINs, extract metadata and use Elcomsoft Distributed Password Recovery instead.
Once you boot the computer into Elcomsoft System Recovery and accept the license agreement, you will see the program’s main window. Click SAM - Local User Database:
Then select the target computer's system drive:
Click Change local user account:
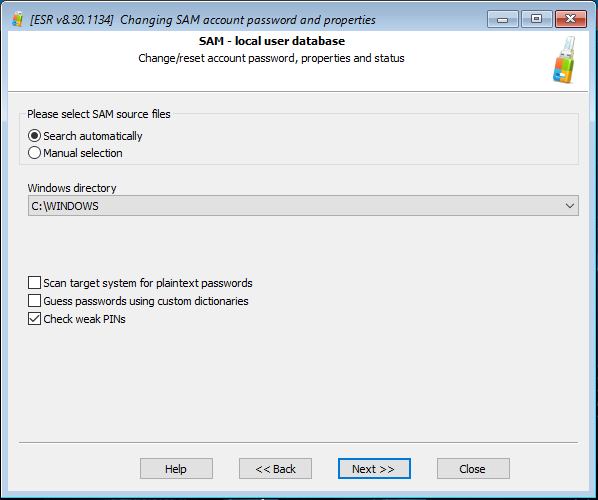
Set up the attack as shown on the screen shot below (the "Check weak PINs" option must be selected):
The tool will then detect user accounts protected with PIN codes, and automatically run a brute-force attack. Once the PINs are discovered, they will be shown in the corresponding window:
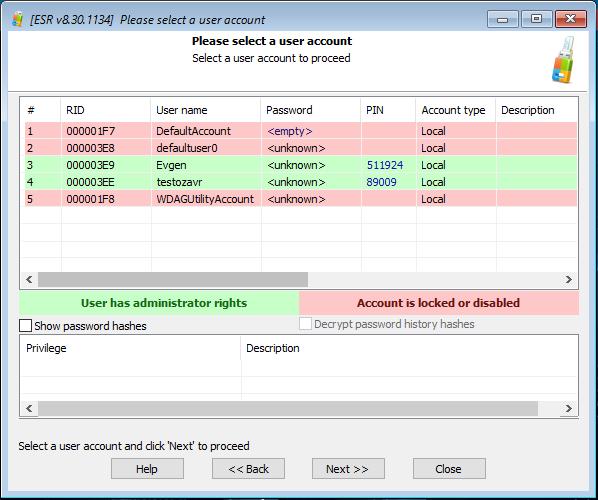
Here's how long it takes us to enumerate all-digit PINs on a 7 year old Intel Core i7-5930K CPU @3.5GHz:
•All 4 digit PINs: 2 seconds
•All 5 digit PINs: 18 seconds
•All 6 digit PINs: 2 minutes
Checking all 4-digit, 5-digit and 6-digit combinations takes up to 2:20 min. If there more than one PIN-enabled account is present, the attacks will be performed separately on all accounts - quite unlike the attack on NTLM hashes, which can be recovered all at once due to shared salt. Interestingly, we discovered that even deleted accounts leave enough traces to launch a PIN attack.
Note: Alphanumeric PIN codes and all-digit PINs that contain more than 6 characters must be attacked offline with Elcomsoft Distributed Password Recovery (update required).